CAN Bus Sniffer - Reverse Engineer Vehicle Data [SavvyCAN/Wireshark]
Need to 'reverse engineer' CAN data from your vehicle?
In this intro we explain how to hack your car/truck to decode proprietary data - letting you convert the raw CAN data to physical values.
In contrast to most guides, we'll make this practical and replicable with outset in the CLX000 CAN bus sniffer and our free software tools.
Tip: See also our SavvyCAN intro - and our new CANmod.router for pro specs CAN-USB streaming.
With the CLX000 CAN analyzer, you can stream CAN bus data from any CAN based application - automotives (cars, trucks, motorcycles, ...), ships, machines etc. Below we take outset in the case of streaming from a car.
To stream raw CAN data involves 4 steps:
- Configure your CLX000 (e.g. to request OBD2 PIDs)
- Connect your CLX000 to your car via an OBD2 adapter
- Connect the CLX000 via a USB cable to your PC
- Start the streaming via the free software
For details, see the CLX000 Intro.

Top 4 benefits of CAN bus reverse engineering
Using the CLX000 and SavvyCAN for reverse engineering CAN data offers key benefits:

Decoding of proprietary data
The most common purpose of 'CAN bus hacking' is to enable the decoding of proprietary CAN IDs to be able to analyze data from e.g. cars, trucks, machinery, etc

Extension of DBC databases
Often, you may have a partially complete CAN database (DBC) - here, a CAN bus decoder tool can help reverse engineer the missing CAN messages and signals

New use cases unlocked
In many use cases, being able to reverse engineer just 1-5 parameters can be make-or-break - e.g. being able to log state of charge (SoC) from electric vehicles.

Asset control via commands
A key benefit from reverse engineering raw CAN data (as opposed to e.g. OBD2) is to enable 'control' of e.g. vehicles via commands (e.g. to toggle lights, locks, ...)
Unsure if your use case would benefit from reverse engineering? Reach out for free sparring!
Contact usHow does CAN reverse engineering work?
In the following we outline how vehicle reverse engineering can be done, step-by-step.

Assume you need to log data from your windscreen wipers. To do so, you first need to identify which CAN ID contains the data. Two methods exist:
Stream data in real-time: Here you use a CAN interface to stream raw CAN data. You will typically then use a CAN bus sniffer software tool to filter irrelevant CAN IDs and gradually isolate the relevant CAN ID by elimination. In the wiper case, you would turn the wipers on/off physically while analyzing the real-time data output.
Log data to an SD card: For some parameters (e.g. EV state of charge), monitoring live data is not practical. Instead, you can e.g. set up a camera to record your vehicle dashboard while logging raw CAN data to an SD card. This lets you manually create a timeseries of "true values" (from the camera) that you can compare vs. your raw CAN data to identify CAN IDs and databyte patterns that correlate with the true values.

At this stage, you have identified which CAN ID contains your wiper data.
A single CAN frame/message typically contains 1-8 CAN signals in the data bytes, i.e. the actual parameters. A signal can e.g. be the wiper 'state' (on/off). The next step is to identify which of the 64 CAN data bits relate to this specific signal.
To do so, we recommend the below steps:
- Identify which of the 8 databytes change in response to changing the wiper state
- Identify which of the bits in the relevant byte(s) change (e.g. in Excel)

Once you know the bit position/length of your signal, it is time to "scale it" via a linear combination of offset and scale. If this is unfamiliar, check our intro to CAN bus. In short, the equation is as below:
physical_value = offset + scale * raw_value_decimal

In the wiper case, the signal may be a boolean (on/off) - and you may simply set the offset to 0 and scale to 1.
For 'continuous' variables (speed, SoC, RPM, ...), you may follow below steps:
- Log CAN data while driving and recording the 'true parameter value' from e.g. the vehicle dashboard using a camera
- Create a plot in e.g. Excel of the unscaled decimal value of the signal vs. the (manually) timestamped true values
- Set a zero offset, overlay the two plots and adjust the scale to "match them"
- Finally, update the offset to ensure a direct overlap between the graphs
The above process is easier if you can log smooth transitions from MIN to MAX of the parameter. Also, if your parameter has an OBD2 equivalent (e.g. RPM, Speed, ...), it can be helpful to compare vs. the logged OBD2 data for faster analysis.
Once you have identified the bit position, length, scale, offset and optionally min/max values, you can add the reverse engineered CAN signal to a CAN database (DBC file), aka a vehicle CAN bus database. This makes it easier to use the decoded signal as part of data processing in most CAN tools. See also our intro to DBC files

Below, we list a range of useful guides for vehicle reverse engineering:
- Hackaday: Great set beginner tutorials on how to hack your CAN bus
- Kenny Kuchera: Cool step-by-step guide to hacking a car (incl. good deep-dives)
- Alexandre Blin: Awesome 'backup camera' vehicle hack with an exciting walkthrough
Get the 'OBD2 Data Pack'
Want to try working with real OBD2 data?
Download your 'data pack' including:
- Our OBD2 DBC
- 25+ car DBCs (reverse engineered)
- 100+ MB of data from 10+ cars
The CLX000 CAN bus sniffer
In the next section, we show how the CLX000 can be used as a CAN bus sniffer.
The CLX000 is a low cost CAN bus data logger & interface, which can be used for real-time CAN streaming with SavvyCAN:
 PLUG & PLAY
PLUG & PLAY
Configure in 2 min. Power via CAN connector. Auto-detect bit-rate
 STANDALONE
STANDALONE
Log CAN data to 8-32GB SD card for months - no pc needed
 FREE SOFTWARE
FREE SOFTWARE
Configure your CLX000, stream data & convert log files
 LIVE STREAM
LIVE STREAM
Easily load, stream or transmit CAN data in SavvyCAN
 COMPACT
COMPACT
Fits the palm of your hand (6.6 x 4.3 x 2.4 CM) and weighs <50g
 learn about the CLX000
learn about the CLX000
Some online blogs and examples of automotive hacks use Arduino modules and CAN bus shields to build low cost CAN bus decoders. In particular, this may appeal to hobbyists who are familiar with Arduino boards and CAN bus shields. Similarly, various Raspberry Pi modules with CAN bus modifications exist that can serve as CAN bus sniffers. There are even examples of ELM327 modules being used for CAN sniffing.
Generally, modules like the Arduino and Raspberry Pi are versatile - but not designed specifically as CAN bus interfaces.
As such, the CLX000 offers a great alternative:
- The CLX000 is plug & play with 100% free software tools, letting you quickly focus on CAN sniffing
- You can easily configure the device - e.g. with CAN ID filters to focus on specific messages of interest
- The SavvyCAN/Wireshark tools provide a user-friendly GUI for analyzing the raw CAN data - and DBC decoding it
- Once you've identified relevant signals, you can create a DBC and use the free SavvyCAN software to decode CLX000 log files
- The CLX000 CAN bus analyzer is both a CAN logger and CAN-to-USB interface - making it a flexible CAN hacking tool
- We provide 100% free and fast support if you have technical questions regarding the CLX000 or software
- The price of the CLX000 is low - and typically lower than the Arduino/Rasperry Pi if the time-to-get-started is considered
If you are in doubt what solution is best for you, please contact us.
As part of reverse engineering your car data, you may want to test whether a specific CAN frame can be used to trigger certain behavior in your vehicle. For example, you may want to unlock your door, blow your horn, turn on the wipers, toggle the radio or manipulate your car dashboard.
To do this, you'll need to send specific CAN frames into your CAN bus with the right CAN ID and data payload. If you're successful, the vehicle may respond accordingly - though some cars may have functionality that block such attempts.
The CLX000 lets you setup custom transmit lists for periodic transmission - as well as real-time control of data transmission via SavvyCAN (via USB). With this, you can e.g. send custom CAN frames, playback log files into your CAN bus - or perform advanced fuzzing. With that said, we recommend that you only do so if you know what you're doing. Generally speaking, it's one thing to use CAN sniffing and CAN bus decoders to extract information for the purpose of e.g. visualizing your car data - it's very different (and risky) to use CAN hardware to try and control your vehicle.
An alternative use case for the CLX000's ability to transmit CAN data frames is to request OBD2 data. ODB2 data can offer easy access to continuous parameters like speed, temperatures, rpm etc. - which may provide useful for side-by-side comparisons when you're e.g. trying to reverse engineer correlated data parameters.
Case study: Motorcycle sniffer
Learn how Thomas Cobb successfully used the CL2000 to reverse engineer CAN bus data from his Ducati Diavel 2015 using both USB streaming and data logging. Thomas also primarily used SavvyCAN in his work.
"The CL2000 is compact, feature rich, highly configurable - and it just works great!"
full case study 30+ case studies
Example: Reverse engineering via SavvyCAN
SavvyCAN is now our recommended default tool for CAN bus reverse engineering with the CLX000.
Below we outline how the various reverse engineering steps can be supported via SavvyCAN.
Tip: You can also check out the excellent tutorial by Dan Dulac using the CL1000 and SavvyCAN in practice!
Start streaming raw CAN data
Start by connecting your CLX000 to your CAN bus and connect it in SavvyCAN to start streaming raw CAN data. This lets you view raw CAN frames and get an initial overview.
You can use the auto-scroll mode or overwrite mode to view the raw CAN frames - and you can easily filter which CAN IDs to display.
Connect "discrete events" to CAN frames
Using the 'sniffer' view in SavvCAN, you can get a quick trace view of all unique CAN frames. The view also highlights changing data bytes/bits, making it easier to link physical events (e.g. locking/unlocking a door) to the CAN data.
You can use the CAN ID filters to gradually isolate your way to the relant CAN ID and CAN data bytes/bits.
Connect "continuous data" to CAN frames
If you need to reverse engineer continuous signals like speed, RPM, temperatures or SoC%, you may find it easier to use the SD card logging of the CLX000. For example, you can drive for 10 minutes in your vehicle and note down the dashboard RPM values with timestamps, then create a rough plot in e.g. Excel to serve as a benchmark.
You can then load your CLX000 log file in SavvyCAN and use the 'range state view'. Here you specify a hypothesis in regards to which CAN IDs may contain the RPM signal, as well as how the signal may be packed in the data bytes. SavvyCAN then plots all possible combinations for comparison vs. your benchmark plot from Excel.
Learn how to "control" your vehicle
If you're looking to identify what CAN frames "control" certain parts of e.g. a vehicle, you can utilize the CLX000 'live-transmit' functionality to e.g. send custom CAN frames into your vehicle - and determine the response in real-time. This is ideal if you e.g. believe you've found a certain functionality, but you wish to quickly test it before proceeding to a more time-consuming implementation. See our SavvyCAN intro for examples of useful live-transmit tools available.
Develop & test your DBC file
Based on your analyses, you'll gradually be able to identify relevant CAN frames and byte/bit positions. Using e.g. the built-in DBC editor in SavvyCAN (or our online DBC editor), you can start by adding this information with scale factors of 1 and offsets of 0.
With this DBC, you can create plots of your data (in real-time or from log files) to identify how your scale/offset factors should be adjusted in order to match your physical observations. For example, if your trip had a max speed (km/h) of 55 and your data shows 110 using a scale factor of 1, you can try adjusting it to 0.5.
Originally, the CLX000 only integrated with Wireshark, for which we developed a set of useful features for CAN reverse engineering. Since then, we have added SavvyCAN to our list of integrations - and we generally believe it is superior for most CAN bus reverse engineering use cases. However, if you e.g. have prior experience using Wireshark, you can of course still use that tool. Below is an example of how to achieve similar steps as shown for SavvyCAN above.
In the following, we illustrate how you can do the reverse engineering steps #1 and #2 using the CLX000 in Wireshark.
Streaming raw CAN data
When you first start streaming raw CAN data with the CLX000, you will get a lot of CAN packets on your screen.
Wireshark provides multiple tools for analyzing this view (filters, column configuration, plots) - but none of them are ideal for the initial reverse engineering efforts.
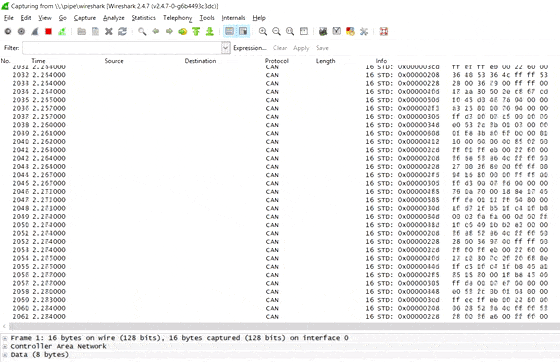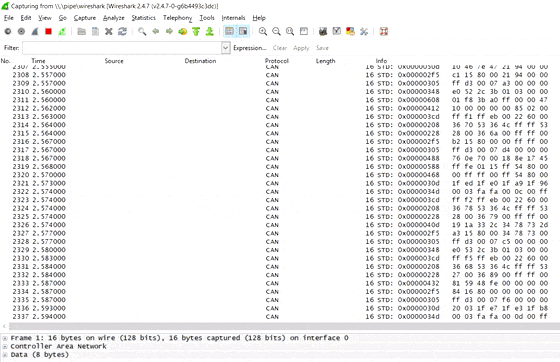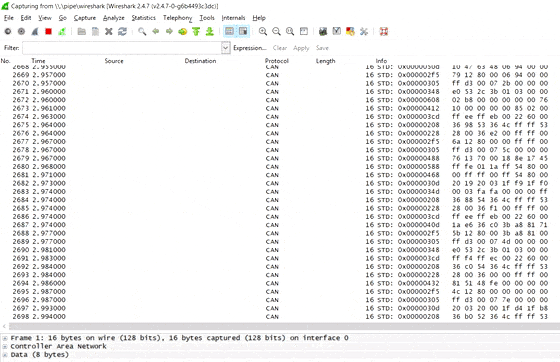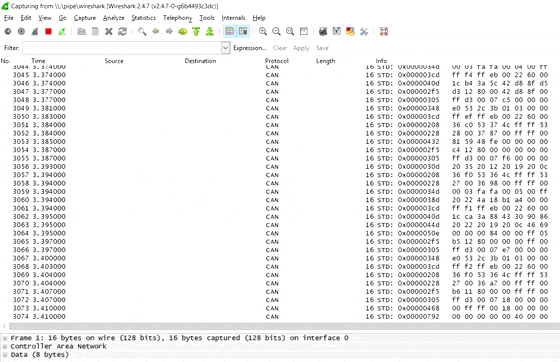
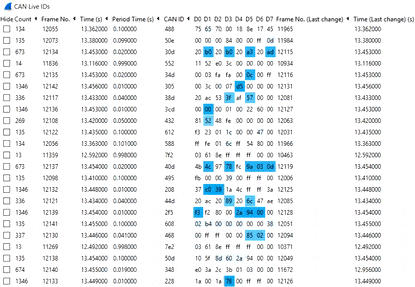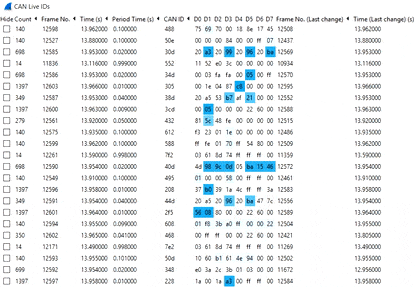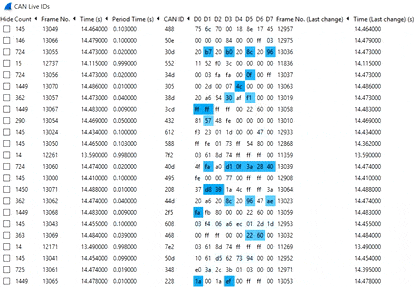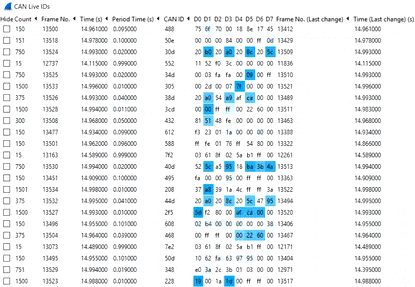
Using the 'CAN Live' feature
Instead, we recommend to use the CAN Live Wireshark plugin feature - which lets you show a 'trace' of your data.
To open this, click Statistics/CAN Live IDs when streaming to bring up the trace window. As evident, this view shows one row for each CAN ID - providing a great overview for CAN hacking.
When a CAN bus data byte changes, it is colored blue - and the color fades as the byte stays constant. This provides immediate visual feedback when comparing raw CAN bus data patterns versus physical events (e.g. turning on the car wipers). In practice, this helps turn Wireshark into a powerful CAN bus decoder software tool.
Ready to reverse engineer your CAN data?
Get your CLX000 CAN decoder today!
